Who am I?
My name is Adam Arrowood and I work for the CyberSecurity team of Georgia Institute of Technology in Atlanta, GA USA. I specialize in web server and web application security.
What do I do?
One of my duties for Georgia Tech is to look for websites hosted on our campus, and on other University System of Georgia (GA USG) domains, that have been compromised and are serving ads for illegal pharmaceutical sales, counterfeit goods, illicit software sales, etc. These ads are known as “backlink spam” and I have authored a website about our effort to fight backlink spam at Georgia Tech.
How do I find compromised websites?
I search for compromised sites by making targeted searches at Google and Bing for terms and phrases that appear on sites serving spam ads. I normally limit these searches to domains that are a part of the GA USG. E.g.:
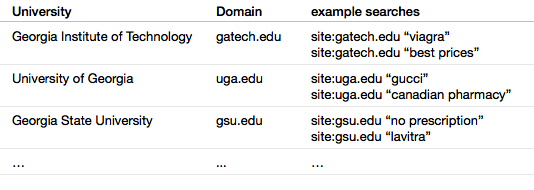
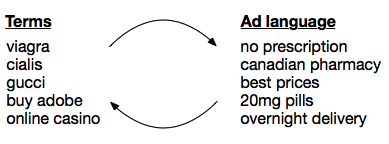
The terms and ad language phrases that I search for change; they complement each other in a feedback loop in which searching for terms in one category helps to find additional terms or phrases to search for. For example, a search for “viagra” will show results that include the phrase “best prices”; subsequently searching for “best prices” will show results that are advertising additional drugs.
Why am I contacting you about a website on your campus?
Most of the time, my searches are limited to domains that are part of the GA USG. However, in order to tune and expand my list of terms and ad language, I occasionally expand my searches to the entire .edu domain space (e.g. I might search for site:edu “canadian pharmacy”). If I come across a significant compromised website that belongs to a major university, I will usually try to contact them and let them know what I’ve found. If you are reading this web page, you are likely to be involved with one of the websites that I have found in my search results.
What do I want you to do?
The first thing you should do is to make contact with your University’s Information Security department and inform them of my contact with you and of the problem that I am reporting. They should be able to advise you on your next steps. If you don’t have an IS department and are on your own in dealing with the issue, you might want to start with a site that Google provides entitled Webmasters help for hacked sites.
If I ask for a copy of the malicious code that is on your site, why am I asking and what do I plan on doing with it?
If I believe that your site has code on it that was installed by hackers in order to serve spam ads, I might ask for a copy of the files containing (only) that code. My interest in the malicious code is threefold:
- To observe what techniques are being used to serve the ads and the “business logic” involved in deciding which ads, if any, to show to website visitors. This, I hope, will help me find additional compromised websites.
- To search the contents of many of our websites at Georgia Tech for the same or similar scripts. We host much of our external-facing websites on a central service and I can scan the contents of all of those sites for scripts matching what is found on your site.
- To find the hostname/IP address of the master ad server that your website is likely contacting. On many compromised sites that are serving ads, the spam links and language being served is not present in any files on the server; instead, for each request to the compromised site, a separate, back-end request is made to a master ad server that sends back the ads or instructions on how the webserver should respond. By looking at netflow data across our campus network border, I would like to see if any of the websites on our campus are talking to the same master ad server as your site.
I will likely share that IP address with other GA USG Universities and with the various security organizations in which Georgia Tech participates. I will not identify your server as the source of the IP address.
If you don’t feel comfortable with sharing, or don’t wish to go to the effort to identify and share the code, that’s ok, too.
How do I contact you if I have code I’m willing to share or if I have further questions about your contact?
Feel free to reach me at adam.arrowood@security.gatech.edu or to call me at (404)-894-9629. If you are sending code and wish to use PGP to encrypt your message, you can find my key below.
Thanks,
Adam Arrowood
-----BEGIN PGP PUBLIC KEY BLOCK----- mQENBFNqdw0BCADN7VbqVE/sm2L6/35J5+j4h0ZiuDyA1H8h7IXwhsiyB3dhTC7h fd3QiKBexOp3ItKvZNznRGcjdH8k3wIBFgB7G4UC7ClmtjTrD4dsZ9T4Tsup3SaH sirG6lEKcVlD8Z0LciWOFBcQeQR/U8+q3ogisYCuDj3comBaQg1sraDvPD9RKLBV mOCdv3WihYLHtsxP/4Ct18jeI8A4BS26Wa8RXtKJg52LyCo1BEn+4kXTyV0A9HBQ v+xaDpxIsMzzTtddQ0o1yww7SB8/NwLLuthu2HJAKuG/Tmpkc/DQ1d0EvSbu7D6V C8vlCYEkfgwhgpC1xMPEvmDdHBmCFWfVpRErABEBAAG0MUFkYW0gQXJyb3dvb2Qg PGFkYW0uYXJyb3dvb2RAc2VjdXJpdHkuZ2F0ZWNoLmVkdT6JATkEEwEIACMFAlVf QOMCGwMHCwkIBwMCAQYVCAIJCgsEFgIDAQIeAQIXgAAKCRDRgLyn6CJ6h7/nB/44 zFSFgb6lCF3hFAaHiHAbR53L2eQPBAPFy2RKWlG14Yam13v6e08DpsSVCpx/vi5J aca3tNgKiTNltq5acT4zbKv/O3qXxYBY1JfPJE4NqnEkRM7v86Egf5GjGIppIcXT H337a6hSUo299BVMn+Nh1bRBpkLF3WkGx/xRX+1UnZCMUUI6uv+vrrkPwlShEm3j QGAp/PRSUJKe4rj+pYZ5I7hOPZbsoVPJyY5TpVd5uWJRJITQz0lPOkQdekEzHPMh bKgO738BdqiEJbFylons2+gJNY28yMKErDAjWw9IwGUHUuGiBKApa7ZVO4fY8+gB GiXlQIz6+ANIt+Oq0kjBtCxBZGFtIEFycm93b29kIDxhZGFtLmFycm93b29kQG9p dC5nYXRlY2guZWR1PokBOwQTAQIAJQIbAwYLCQgHAwIGFQgCCQoLBBYCAwECHgEC F4AFAlVfQOkCGQEACgkQ0YC8p+gieofyDwf9FheY7f759d8Yh15tI8kggqnl/0CC PUIn91PLT4wb/f93upmV9YcC+xGxCTg2Oog8ga5lKxgoserO7fdDZV1f2rEy7S1M xcIjoyoqwzdJgSPjIVG3Tt09gq0UuXqFXjWH69XWNj6As5qJdTE15flvmjqww4us yWMCypyJy/hMfZ7dFWiwy05eJ+YFQml0KsAuHL4XGmknaeoQqQIJngLqp9ZAEHGa 57fof7K7RMP1Y0s/b9dDvEtxOZVcLg4i3a023QD+vNLw9/pmn6UvhbQTWNkmmp/H sZeVbE6p5hPEi9N72MMDmXLwtuIWIO7NPkTtB5qQekViga4JGllknyc6yLkBDQRT ancNAQgA7rJDW/2sDeksY8pErlKC6QcYXoKATE3r8Uwu/d6RO7wAsFnB7T8ib2fO 4OhK6PMu+XRVUXIWuo35p2pC9WXYi+3A77khrgZKMlZk2cEeHbt1ljFYJK9CryQz HqwR2n5EbHynEqe8iqtvbc7QjH6q3JfbreVrpqiOCMMnnqo6iiFexfyAsxY1nzdt m6R/qeR4KD6SLSKidUP99D447+nF/Xaes+8kKop12PGzt1XOSqQafZHvXWjP51aM oB/c7LfrHt+OlKQxmidWGe5n+oM0W19WTisOSgtHBXcBflc1e6dJT9jDyHh97KCm CAnoKtGQJAbtvbuJuLf45r48QyOpnwARAQABiQEfBBgBAgAJBQJTancNAhsMAAoJ ENGAvKfoInqHU4IH/3ZTMM3sXN6T6wVcceFCYyB6uGgXB8T+bkeWCTRf8ZS0JdPn kccH8ru9QW8ZHV2d7o94biaUXOgfGTVFtKN8qif5uIeybbkpqQhFf9GtgnUyaXm/ qKNapNmygxrD6bd5XJyigchLbxpuDcUjSwUCBvu28q2MRriiY8XiIRbwDZw8Gboh ifNfp7gJ7AgVfT92JMTjWBjVRHald8+V79ySEchJ/cvKOQoE8SLWgG1GuETHjioH jCUHwz7YvOd6nmfsxBArx5T/8XdKi+KE55hoUiZU+I6Oy3V23piMJfFVwukbtWq1 EuYJLSzwXLzClWOsEusBCNO+7D+VUwJhqAeMfoc= =3BTw -----END PGP PUBLIC KEY BLOCK-----

